What is a VPN?
Something that the typical Internet user has likely heard of, but has never truly explored in depth is the VPN, or the Virtual Private Network. The technology has existed since 1996, theorised to have been invented by Microsoft employee Gurdeep Singh-Pall1, and has grown immensely in popularity over the last decade. The purpose of a VPN is to create a private world within the public Internet - to secure information away from surveillance, hackers, and prying eyes - and ensure that any connection between devices and people is shown only to authorised users2. It does this by faking the user's location, computer identity, and wrapping data in many layers of security to protect it3.
As digital citizens grow more concerned about privacy - with a 2019 study by VPNMentor showing that 45% of Internet users are more concerned about their privacy than they were a year ago4 - VPNs climb in popularity. The study also revealed that VPN usage nearly tripled between 2017 and 2018, with a further 165% growth between 2018 and 2019, and an expected 2019 market revenue of $23.6 billion5.
What can I use my VPN for?
However, tighter privacy is not the only thing a VPN boasts - as the main security feature is spoofing your geographic location and server identity, it also provides the ability to6:
- Access blocked content if your work, school or home network has blocked access to certain websites.
- Access geo-restricted content if you are trying to access content that is limited to certain geographic regions (entertainment sites such as YouTube and Netflix frequently geo-block).
- Access censored content, especially if you reside in countries who censor Internet for their citizens (such as China, Indonesia and Saudi Arabia).
VPN usage is consistently highest in countries with censored internet, such as Indonesia where 38% of Internet users have a VPN. In China, 31% make use of a VPN7, to bypass the 'Great Firewall of China', which was put in place to filter and remove 'unacceptable' content and maintain 'social order'8. While many of these countries have a ban on VPNs, often implemented by banning known VPN servers, users and sometimes even banning any international traffic, there are still many available that host special servers to circumvent this system.
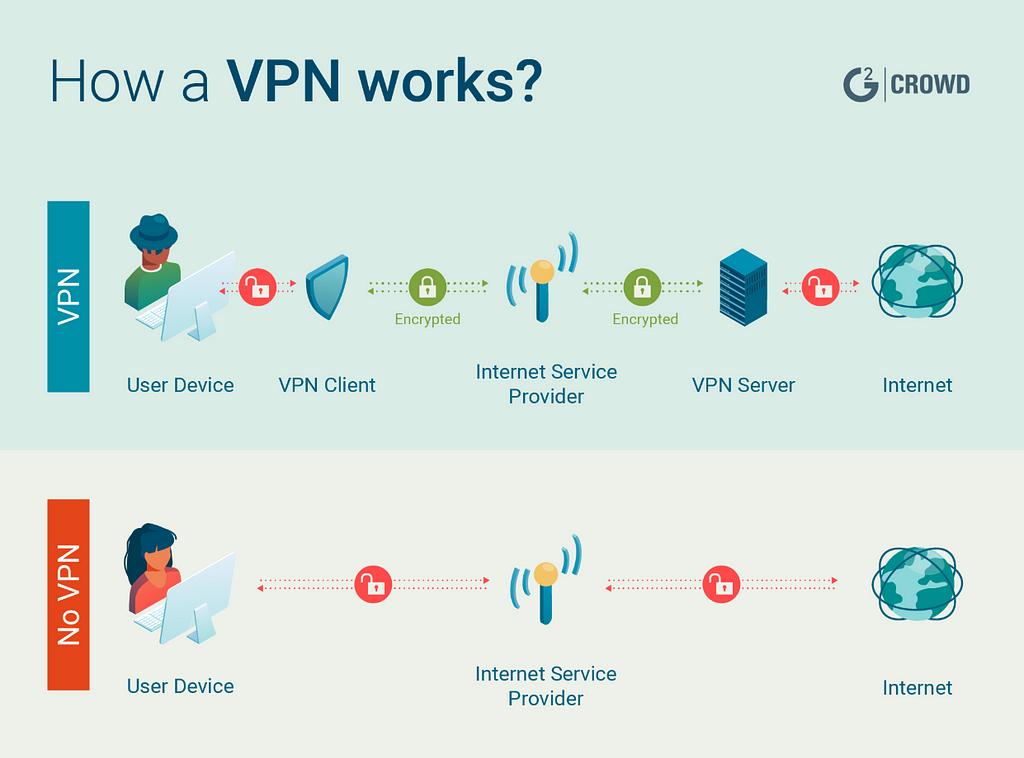
How exactly does a VPN accomplish this?
To contextualise this, think of a home router and modem - when you connect a device such as a smartphone to Wi-Fi, it connects to the router. That groups these devices together in order to facilitate inter-device communication and combine it into one cohesive package, which links to your modem, typically with a physical cable (an Ethernet link)9. The modem is what connects to the Internet through your Internet Service Provider, or ISP.
This is what is referred to as a private network - a collection of devices all operating in the same 'family', that only authorised users can access. VPNs operate in the same way, only virtually - the physical router creates a tangible network, from which Internet access can be cut at any time by removing the Ethernet cable. Using a VPN, the router simply exists on digital devices such as a computer or smartphone.
To explain further, let's discuss the IP address. Your router is automatically assigned this Internet Protocol address by your ISP10. This address covers everything connected to the router's private network, meaning that any device using the router will be tagged with that IP address. Nearly every website, platform and network on the Internet will track this unique identifier to uncover your information, which is often used in nefarious ways.
For example, Australia's NBN Co. proposed that ISPs should be able to charge more money to customers who use entertainment streaming services - as when your ISP can monitor your IP address, they can monitor what Internet traffic has been routed through it11. The United States' net neutrality repeal - put simply, the repeal of the law that states ISPs must treat all Internet traffic equally - also spells disaster. Without net neutrality, ISPs may throttle your bandwidth (slow down or virtually stop connections to certain content), as well as track and sell your browsing history12.
Regarding VPNs, think back to the router and modem. The router 'middleman' still creates paths, but is hosted on a server that is unique to each VPN provider and can host multiple IP addresses. The address you connect to will depend on which country and which server is chosen, but there are countless ones available to be used by every user of that specific VPN. This digital router reconnects to our physical modem, to then be forwarded to the Internet as usual, only this time no-one can see your activity. That can only be tracked as far as the router, at which point it is visible that you have re-routed through a VPN, and nothing more13.
What makes your VPN traffic private?
Using the Internet unprotected is like sending a letter. The letter has a return and delivery address, and the content inside. This is analogous to your device that sends the traffic, the webpage addresses you're accessing and the information that your device is communicating to the address, such as any passwords, usernames, and personal details. This letter goes into the post-box, which acts as our router - amalgamating information - and then to the postal delivery service, which acts as our modem - sending information where we intended it to go. At any point, someone could break in to the post-box to take our letter, or a meddling worker could open it and read the information inside. If this occurs on an online unsecured network, anything from your passwords to your banking details becomes visible.
To avoid someone intercepting this data, the main - and widely considered strongest - security method is encryption; making it unreadable to everyone except the intended receiver14. Essentially, encryption is like putting it through a scrambler to mix it up using a certain formula, or key. This creates the encrypted ciphertext. This is symmetric encryption, where whoever has access to the key is able to use the key to decode and extract the original content - the plaintext. However, the key has to be sent somehow, and if it is sent in the same manner as the encrypted text, then anyone who intercepts your traffic can use it, effectively making the encryption useless. Therefore, we need a way to exchange the key secretly, ensuring that the intended recipient can use it and others cannot - one of the most popular methods for this being the 'Diffie-Hellman Key Exchange', or public-key, asymmetric encryption15.
A popular analogy for this method is as follows:
- My friend sends me an encrypted message.
- I send my friend a box in the mail, which contains an unlocked padlock.
- My friend puts the code that can decrypt the ciphertext in the box.
- My friend locks the box, using my padlock, to send back to me.
- I receive the box, and unlock it with my padlock key.
- I decrypt the message into plaintext with the code.
Now, imagine that the unlocked padlock is the public key; something anyone can use for locking or encrypting
purposes. The padlock key is the private key - it has been specifically designed to crack whatever the public key locks, but I am the only one who can access it. Online, these private keys are also infinitely more secure
than a physical lock and key, typically extensive strings of unguessable numbers, with most estimates stating
that one key would take approximately a few quintillion years to break16. Many VPNs have other security measures, such as a 'Kill Switch' which disconnects from the Internet if the VPN is compromised - this assures total privacy, especially important for those in countries with censored content and bans on VPNs17.
Attached below is a YouTube video on the topic, that proposes another analogy and touches on the more in-depth mathematics involved in true asymmetric encryption.
Why do I need to know?
Although VPNs have come under fire for how some criminals use it on the deep and dark webs to mask their identity, and their controversial ban status in certain countries, this has nothing to do with the credibility of the VPN - nor does it mean that VPNs are only for criminals! In fact, 25% of the Internet currently uses one18. They are only as complicit as ski mask manufacturers are when someone wears their product to rob a bank. For most people, the anonymity provided by a VPN is simply a plus: the real attraction is the security and the geographic spoofing that allows worldwide browsing of sites like Netflix, with 50% of users stating that their main use of VPNs is to access entertainment19.
Another point of apprehension is trusting the VPN to not unlawfully log, store, sell or reveal their data. While most VPNs clearly state in their license agreements that they do not, there are still hundreds of untrustworthy VPNs on the market. These are typically free VPNs, who make their money by selling your activity to third parties, negating any anonymity20! They can also spam your service with malware and advertisements, to pay for their servers. The saying "if you didn't pay for the product, you are the product", rings true for VPNs. Unfortunately, there are still 'legitimate' VPN services who have compromised user data, such as when the VPN HideMyAss provided user data to the FBI, proving data logging and storing despite their claims otherwise21.
However, you already probably can't trust your ISP to handle your sensitive, personal data - and you certainly can't trust unsecured networks that can potentially expose it. Therefore, finding a VPN that is trustworthy and transparent about their policies is worth the time and money it takes, as the peace of mind that comes with secure browsing and privacy measures significantly outweighs the cost of any VPN. As the fight for net neutrality continues, authoritarian censorship expands worldwide and cyber-attacks such as data breaches occur every 39 seconds22, a VPN is more necessary than ever for the average Internet user, and it is a crucial tool for anyone concerned about their security online.